In today's rapidly evolving technological landscape, Continuous Integration and Deployment (CI/CD) has become the cornerstone of modern software development practices. However, as we transition into the era of Web 3.0, characterized by decentralized architectures and blockchain technologies, the traditional approaches to CI/CD face a plethora of unique challenges. To effectively navigate this terrain, it's essential to understand the intricacies of Web 3.0 and how they impact CI/CD pipelines.
Understanding Web 3.0:
Web 3.0 represents the next phase of the internet, emphasizing decentralization, peer-to-peer networks, and the integration of blockchain technology. Unlike its predecessors, Web 3.0 aims to provide greater control over data, enhanced privacy, and improved security. Key technologies driving Web 3.0 include blockchain, smart contracts, decentralized storage, and decentralized identity systems.
Challenges of Web 3.0 CI/CD:
Transitioning traditional CI/CD practices to Web 3.0 environments poses several challenges. These challenges stem from the decentralized nature of Web 3.0 technologies, which introduce complexities in testing, deployment, and maintenance. Some of the key challenges include:
Interoperability: Web 3.0 applications often comprise multiple interconnected components, each with its own set of dependencies and protocols. Ensuring compatibility and seamless integration between these components can be challenging.
Smart Contract Testing: Smart contracts, which are self-executing contracts with code stored on a blockchain, require specialized testing methodologies to ensure their reliability and security. Traditional testing frameworks may not be suitable for smart contract development, necessitating the adoption of new tools and approaches.
Decentralized Deployment: Deploying decentralized applications (DApps) and associated infrastructure components in Web 3.0 environments requires specialized deployment strategies. Decentralized storage solutions, consensus mechanisms, and blockchain networks all pose unique challenges in terms of deployment and configuration.
Testing Smart Contracts:
Smart contracts play a central role in many Web 3.0 applications, serving as self-executing agreements with the terms of the contract directly written into code. Ensuring the reliability and security of smart contracts requires thorough testing methodologies tailored to their unique characteristics. Some key considerations for testing smart contracts include:
Unit Testing: Unit testing involves testing individual functions and methods within smart contracts to ensure they behave as expected. Tools like Truffle and Ganache provide frameworks for writing and executing unit tests for smart contracts.
Integration Testing: Integration testing verifies the interaction between different smart contracts and external dependencies. It ensures that smart contracts function correctly within the broader context of the decentralized application.
Security Audits: Security audits are essential for identifying vulnerabilities and weaknesses in smart contract code. Automated security analysis tools, as well as manual code reviews by security experts, can help uncover potential security flaws and mitigate risks.
Deploying Decentralized Storage:
Decentralized storage solutions, such as InterPlanetary File System (IPFS) and Swarm, offer novel approaches to data storage in Web 3.0 environments. Integrating these solutions into CI/CD pipelines requires careful consideration of deployment strategies, versioning mechanisms, and accessibility. Key considerations for deploying decentralized storage include:
Content Addressing: Decentralized storage solutions typically use content addressing to retrieve data based on its content rather than its location. This ensures data integrity and enables efficient content distribution across decentralized networks.
Replication Strategies: Replication strategies determine how data is replicated and distributed across multiple nodes in a decentralized storage network. Strategies such as sharding and erasure coding help optimize data availability and resilience in the face of network failures or attacks.
Versioning Mechanisms: Versioning mechanisms ensure that data stored in decentralized storage solutions can be updated and accessed reliably over time. Techniques such as content-based versioning and distributed version control systems enable seamless collaboration and data management in decentralized environments.
Continuous Deployment for Decentralized Systems:
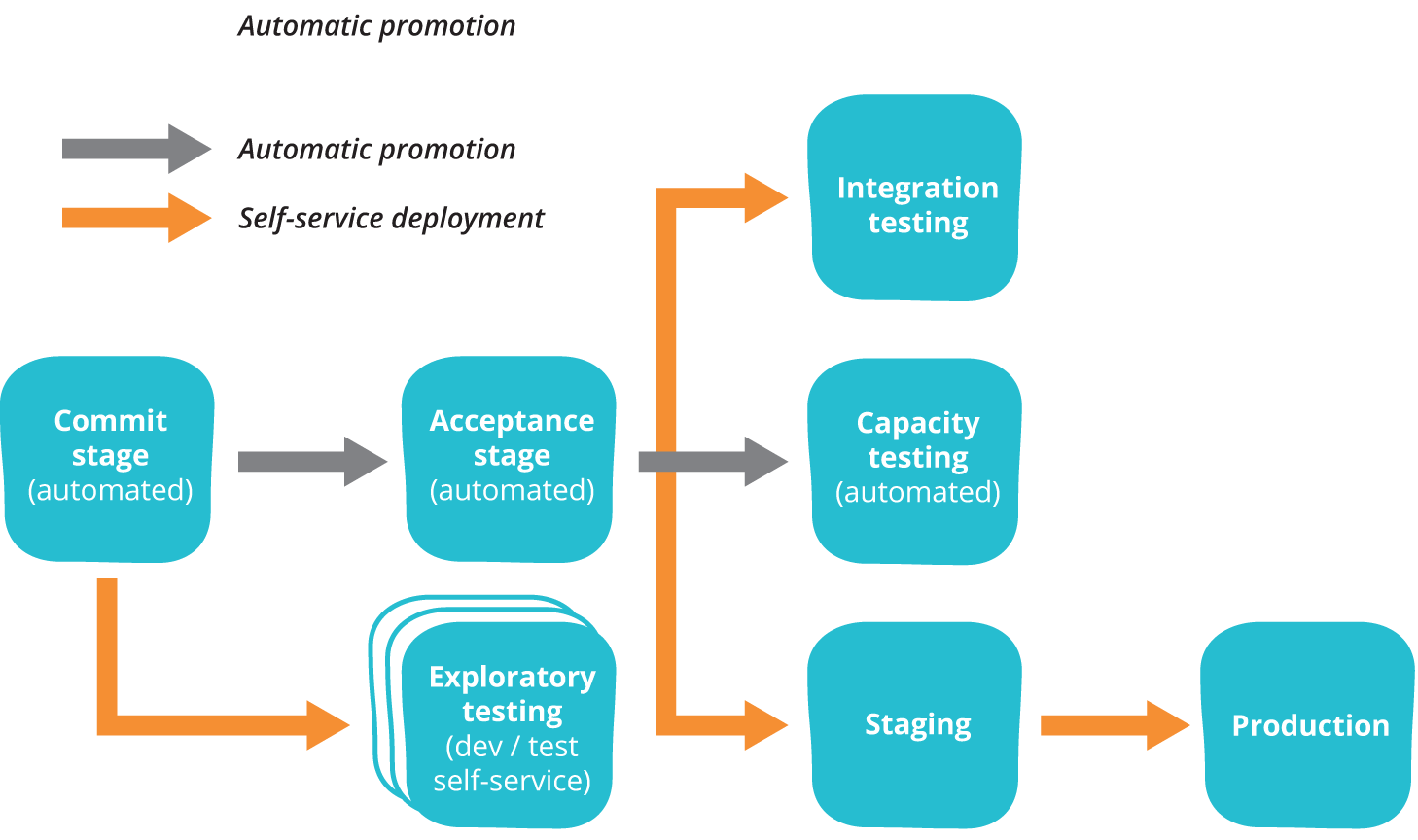
Continuous deployment practices play a crucial role in Web 3.0 environments, where agility and responsiveness are paramount. DevOps teams orchestrate workflows that facilitate the seamless rollout of updates to blockchain networks, smart contracts, and decentralized applications (DApps). Key considerations for continuous deployment in decentralized systems include:
Automated Testing: Automated testing frameworks are essential for ensuring the reliability and security of updates deployed to decentralized systems. Continuous integration pipelines should include comprehensive testing suites for smart contracts, decentralized storage, and other components of Web 3.0 applications.
Deployment Strategies: Deployment strategies such as blue-green deployments and canary releases enable organizations to roll out updates incrementally while minimizing disruption to users. These strategies help mitigate risks and ensure a smooth transition to new versions of decentralized applications.
Monitoring and Rollback: Continuous deployment pipelines should include robust monitoring and rollback mechanisms to detect and address issues promptly. Automated monitoring tools can provide real-time insights into the health and performance of decentralized systems, enabling DevOps teams to take proactive measures to maintain service availability and reliability.
Security and Compliance Considerations:
Security and compliance are paramount concerns in Web 3.0 CI/CD pipelines, given the immutable nature of blockchain technology. DevOps teams embed security testing and compliance checks within the deployment workflow to preemptively detect and neutralize potential threats. Key considerations for security and compliance in Web 3.0 applications include:
Automated Security Scanning: Automated security scanning tools help identify vulnerabilities and weaknesses in smart contract code, decentralized storage solutions, and other components of Web 3.0 applications. These tools should be integrated into the CI/CD pipeline to ensure that security vulnerabilities are detected and remediated early in the development process.
Manual Code Reviews and Audits: Manual code reviews and security audits conducted by experienced security experts are essential for identifying complex security issues that may not be detected by automated tools. These reviews should be performed regularly to ensure that Web 3.0 applications adhere to security best practices and compliance standards.
Compliance with Regulatory Standards: Web 3.0 applications are subject to various regulatory requirements, depending on the jurisdiction in which they operate. DevOps teams must ensure that decentralized systems comply with relevant regulatory standards, such as data protection regulations and financial regulations.
As we delve deeper into the intricacies of Continuous Integration and Deployment (CI/CD) in the context of Web 3.0 applications, it's crucial to explore additional dimensions, including advanced testing methodologies, deployment strategies, and the evolving landscape of security and compliance. Let's continue our exploration:
Advanced Testing Methodologies:
Testing is the bedrock of reliable and secure software deployment, and in the realm of Web 3.0 applications, where decentralized architectures and blockchain technologies reign supreme, the testing landscape takes on a new level of complexity. Beyond the fundamental testing approaches mentioned earlier, several advanced methodologies deserve attention:
Property-Based Testing: Property-based testing, also known as generative testing, involves specifying general properties that a system should adhere to and then automatically generating test cases to verify those properties. In the context of Web 3.0 applications, property-based testing can help uncover subtle bugs and edge cases that may go unnoticed with traditional testing methods.
Formal Verification: Formal verification is a rigorous mathematical technique for proving the correctness of software systems. In the context of smart contracts, formal verification involves mathematically proving that a contract behaves as intended under all possible circumstances. While formal verification can be resource-intensive, it provides a high level of assurance that smart contracts are free from bugs and vulnerabilities.
Chaos Engineering: Chaos engineering is a discipline that involves deliberately injecting failures into a system to test its resilience and robustness. In the context of Web 3.0 applications, chaos engineering can help identify weak points in decentralized systems and validate the effectiveness of redundancy and failover mechanisms. By simulating real-world failure scenarios, chaos engineering enables DevOps teams to proactively address potential vulnerabilities and improve overall system reliability.
Deployment Strategies for Decentralized Systems:
Deploying updates to decentralized systems presents unique challenges compared to traditional centralized applications. In addition to the deployment strategies mentioned earlier, several specialized approaches are particularly relevant in the context of Web 3.0:
Atomic Swaps: Atomic swaps are a mechanism for exchanging assets between different blockchain networks without the need for trusted intermediaries. In the context of continuous deployment, atomic swaps can be used to seamlessly update smart contracts and other blockchain-based components across multiple networks. By ensuring atomicity and consistency, atomic swaps minimize the risk of inconsistent state changes and enable smooth transitions between different versions of decentralized applications.
Immutable Deployments: Immutable deployments involve deploying updates to decentralized systems in a way that preserves the integrity of the underlying blockchain data. Instead of modifying existing smart contracts or data stored on the blockchain, immutable deployments create new instances of contracts or data structures and update references to point to the new instances. This approach ensures that historical data remains unchanged and provides a clear audit trail of all changes made to the system over time.
Upgradeable Contracts: Upgradeable contracts are a pattern for managing smart contract upgrades in a decentralized manner. Instead of deploying a new version of a smart contract and abandoning the old version, upgradeable contracts allow developers to migrate existing contract state and logic to a new version while preserving the contract's address and identity. This approach enables seamless upgrades to smart contracts without disrupting ongoing transactions or interactions with the contract.
Evolution of Security and Compliance Practices:
Security and compliance are dynamic fields that continue to evolve in response to emerging threats and regulatory requirements. In the context of Web 3.0 applications, DevOps teams must stay abreast of the latest developments and best practices to ensure the security and compliance of decentralized systems:
Decentralized Identity Management: Decentralized identity management is a foundational component of Web 3.0 applications, enabling users to control their digital identities and access rights without relying on centralized authorities. DevOps teams must implement robust identity management systems that integrate seamlessly with decentralized applications and adhere to privacy and security best practices.
Privacy-Preserving Technologies: Privacy-preserving technologies such as zero-knowledge proofs and homomorphic encryption play a crucial role in protecting sensitive data in Web 3.0 applications. DevOps teams should explore ways to incorporate these technologies into their CI/CD pipelines to ensure that user data remains private and confidential.
Regulatory Compliance Frameworks: Regulatory compliance frameworks such as GDPR (General Data Protection Regulation) and FATF (Financial Action Task Force) provide guidelines for ensuring that decentralized systems comply with relevant legal and regulatory requirements. DevOps teams must familiarize themselves with these frameworks and implement appropriate controls and safeguards to mitigate compliance risks.
Conclusion:
In conclusion, Continuous Integration and Deployment in Web 3.0 applications is a multifaceted endeavor that requires a deep understanding of decentralized technologies, advanced testing methodologies, specialized deployment strategies, and evolving security and compliance practices. By embracing innovation, staying informed about emerging trends, and adopting a proactive approach to addressing challenges, DevOps teams can navigate the complexities of Web 3.0 development and ensure the reliability, security, and compliance of decentralized systems in the digital age.